The road to efficient Android fuzzing
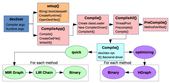
In the aftermath of the recent Android stagefright vulnerabilities, efficient fuzz testing techniques and tools for the Android ecosystem are again in the spotlight. In this post we would like to share some of the fuzz testing experience we have gained through our projects and show how it can be applied in the Android world. Additionally, we’ll enlist some of the public contributions we’ve made to open source tools aiming to help the community focus more on the target and less on the tooling.
Introducing wifiphisher - BSides London 2015
Hello. My name is George Chatzisofroniou (@_sophron) and I work as a security engineer at CENSUS. This summer I gave a talk at BSides London. The talk was called ‘Introducing wifiphisher, a tool for automated WiFi phishing attacks’ and revolved around the recently published tool.
Fuzzing Objects d’ART — Hack In The Box 2015 Amsterdam
Hello, my name is Anestis Bechtsoudis and I’m a security engineer at CENSUS. I recently gave a talk on Android ART runtime fuzzing techniques at the Hack-in-the-Box 2015 Amsterdam security conference. The talk entitled “Fuzzing Objects d’ART — Digging Into the New Android L Runtime Internals”, analyzed a series of DEX smart fuzzing techniques targeting the bytecode optimization and compilation components of the new Android ART runtime.
OR’LYEH? The Shadow over Firefox (INFILTRATE 2015)
About two months ago (April 15th 2015) I visited Miami and presented at the INFILTRATE Security Conference a talk on Firefox heap exploitation, titled “OR’LYEH? The Shadow over Firefox”. The organization of the conference was flawless and the people I met there were amazing. A special thank you to the Immunity team for being great hosts and for their helpful feedback.